- Solution
- Products
Products All Menu View
- Function
- Product/Service
- ONE AI
- OmniEsol
- Amaranth 10
- WEHAGO
- WEHAGO H
- IDC
- The Porter zone
- GEN AI DEWS
- MES
- Amaranth 10 UC
- WEHAGO T
- WEHAGO V
- Cloudserver
- Factoring
- Insight AX
- EFIS
- Argos EIM
- Smart A 10
- Medical Big Data Platform
- Cloudfax
- Electronic Tax Invoice
- ICS
- Argos EDM
- NAHAGO
- Certified E-Document
- Smart Works v4.0
- Local Government Digital Civic Administration Service Platform
- Company
- Media
- Investors
- Solution
- Products
- Function
- Product/Service
- ONE AI
- GEN AI DEWS
- Insight AX
- OmniEsol
- MES
- EFIS
- ICS
- Amaranth 10
- Amaranth 10 UC
- Argos EIM
- Argos EDM
- WEHAGO
- WEHAGO T
- Smart A 10
- NAHAGO
- WEHAGO H
- WEHAGO V
- Medical Big Data Platform
- Certified E-Document
- IDC
- Cloudserver
- Cloudfax
- Smart Works v4.0
- The Porter zone
- Factoring
- Electronic Tax Invoice
- Local Government Digital Civic Administration Service Platform
- Company
- Media
- Investors
- ENG
- Solution
All menu
Products
DOUZONE ICT GROUP provides ICT services that lead enterprise informatization.
Argos EIM to prevent the leakage of important enterprise information
Argos EIM is a solution that blocks and prevents any leakage of important data and intellectual properties beforehand.
The solution monitors unauthorized access to and controls external exports of the essential internal data of the enterprise.
The solution monitors unauthorized access to and controls external exports of the essential internal data of the enterprise.

The best solution to protect intellectual properties
Argos EIM Main Features
- Argos PIMON
-
- Survey Staff PC Information and Status
- Classify based on security levels
- Document Use History Management
- Real-time Monitoring of Information Leak
- Argos DLP
-
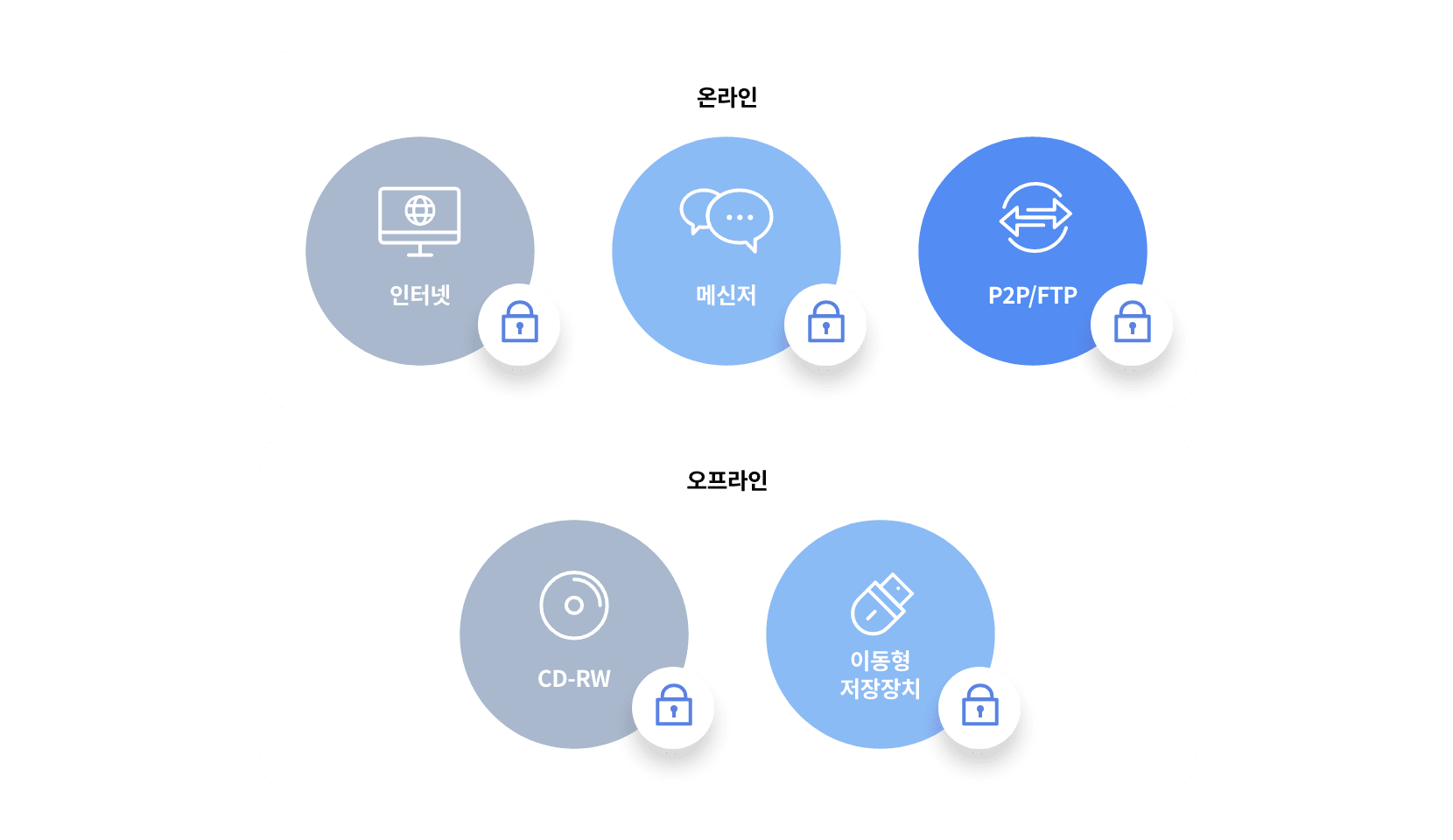
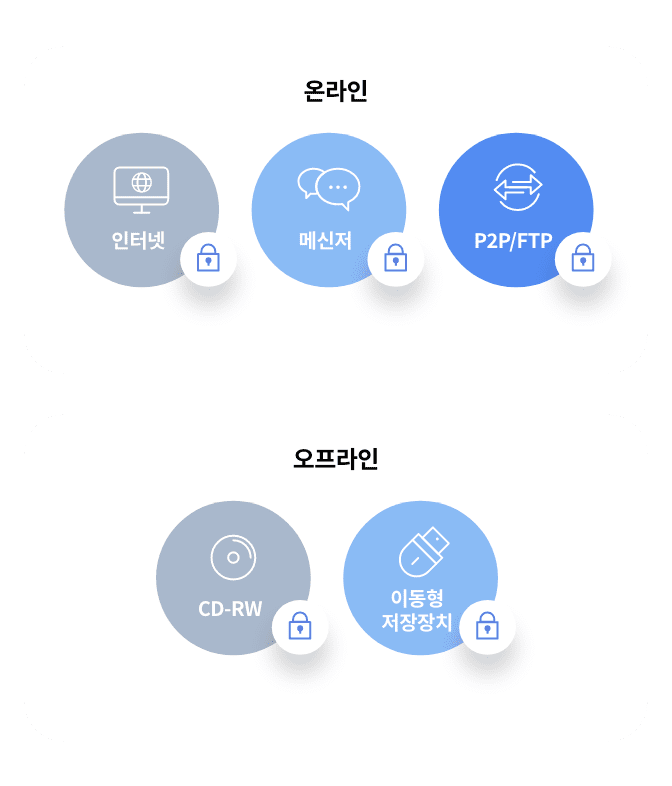
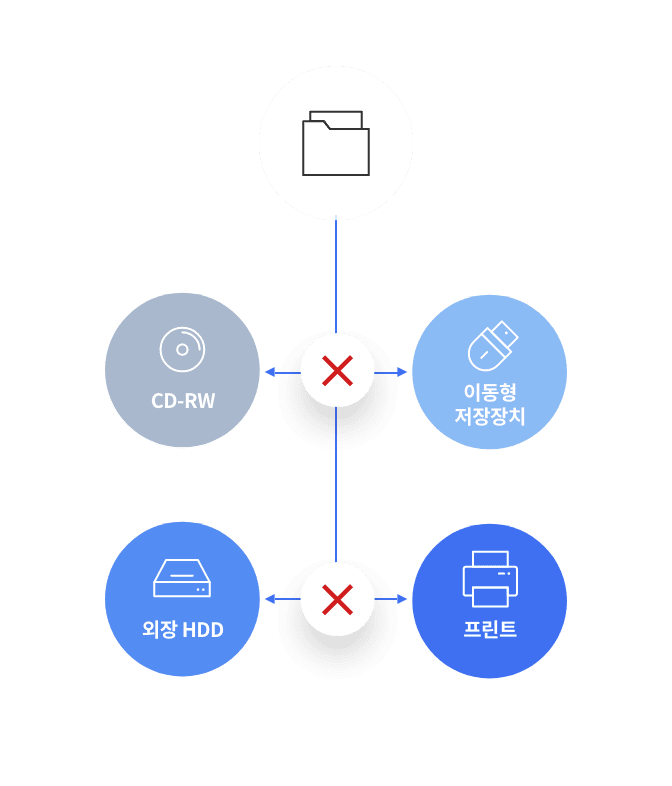
- Online and offline controls
- Storage Media Control Function
- Internet and Program Contro
- Intellectual Property Monitoring
Argos EIM Distinct Advantages
Recommended for
All business types that require advanced detection of violation of internal information control policies or other signs of illegal leakage through lifecycle
(generation, modification, deletion, copy and transfer, etc.) of the sensitive information
(generation, modification, deletion, copy and transfer, etc.) of the sensitive information
- IT services
- Electric
and Electronics - Telecommunications
- Energy
- Chemistry
- Machinery and Manufacturing
- Automotive components
- Franchises
- Distribution
- Services
- Transportation
and Warehousing - Hospitals and
Pharmaceuticals - Cosmetics
- Clothing
and Textile - Defense
- Corporations with Core National Technologies
Benefits
Argos EIM enables you to protect intellectual properties with internal information management and controls
purchasing consultation
1688
5000
5000